Table of Contents
NAV features at a glance
Introduction
Network Administration Visualized is an advanced software suite to monitor large computer networks. It automatically discovers network topology, monitors network load and outages, and can send alerts on network events by e-mail and SMS, allowing for flexible configuration of alert profiles.
Development of NAV started in 1999 at the Norwegian University of Science and Technology (NTNU). It originated as a collection of scripts used internally at NTNU's ITEA Network group. In 2001 UNINETT became interested in its development. In 2006 the development of NAV was moved from NTNU to UNINETT. NAV is used at nearly all universities and university colleges in Norway and many places elsewhere.
As of 2004 NAV is made freely available under the GNU General Public License. NAV runs on a unix platform, software packages are currently available for Debian, RHEL/Centos, Suse and FreeBSD.
NAV functionality
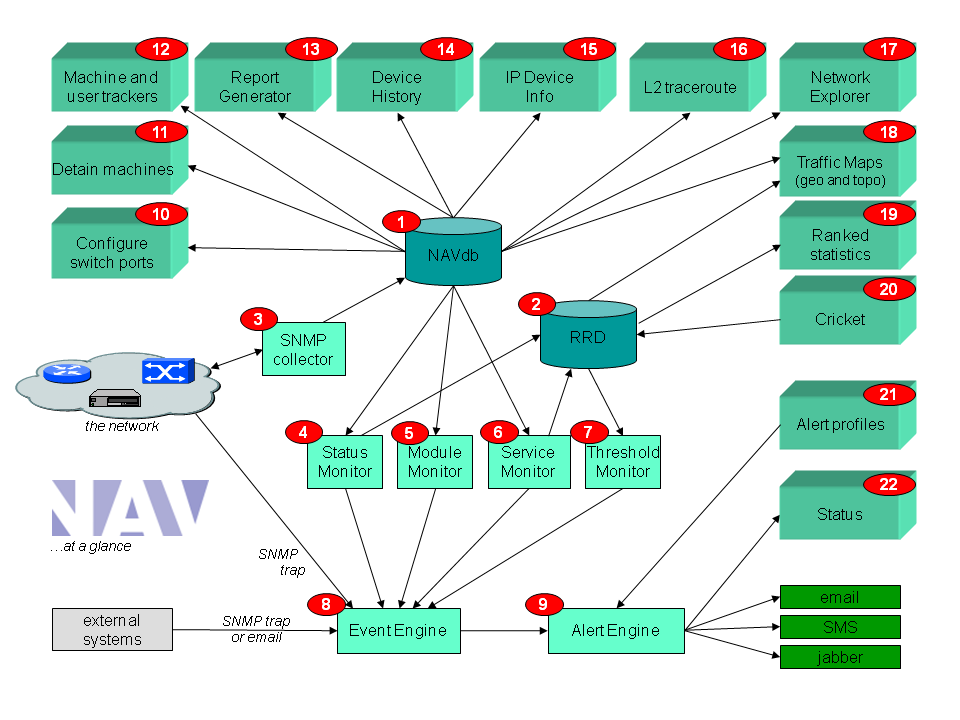
The figure below gives an overview of NAV. As shown, the NAV database is the heart of the system (background processes are on the bottom of the figure, foreground web tools are on the top).
With reference to the figure, and in summary, NAV contains the following functionality:
- A postgreSQL database, NAVdb, (1) modelling the running network. An SNMP collector (3) collects data from the network. The physical interconnection of devices is auto detected, as well as the vlan topology.
- A status monitor (3) that detects network outages. Both IPv4 and IPv6 are supported. For severe cases where many devices are down NAV will try to pinpoint the root cause of the problem (i.e. distinguishing between devices down and devices in shadow)
- Traffic statistics (2,20) for all “intersections” in the network; i.e. all router and switch ports. Octet, packet and error counters are collected, along with CPU and memory statistics, temperature sensors (and more). Use the "ranked statistics" (19) to present a list of interfaces with most traffic, the highest error counts, etc. The traffic statistics collection uses RRDTool and Cricket. NAV automatically builds the Cricket configuration tree for you.
- A machine tracker (12) where you can search for machines and where they currently are connected in the network, or where they have been connected earlier. Search for mac addresses, IPv4 or IPv6 addresses.
- A Mac Watch tool that let you set up a watch list for mac addresses that will trigger alarms if watched mac addresses appear on the network.
- If you use 802.1X authentication in the wired or wireless network (i.e. eduroam), use NAV's radius-base usertracker (12) to search for authenticated users.
- A machine detention tool (11: Arnold) lets you detain machines from the network, either by blocking the access switch port, or change the vlan to a quarantine vlan. A back-end script that easily integrates with external system can run automated detention jobs.
- A network weather map (18, Netmap) that displays the layer 3 and layer 2 topology and current traffic conditions. Dropdown menues give detailed information and links to the traffic statistics.
- A geographical map (18, Geomap) that shows network topology and traffic on an OpenStreetMap. You can view the current traffic conditions or you can step back in time.
- A network explorer (17) giving a graphical tree-structured display of the network on layer 2, also showing spanning tree states. You may for instance search for a particular server and the network explorer will expand the relevant switches to show a network trace to the server.
- A layer 2 traceroute tool (16) that traces the physical path between two machines in the network.
- Reports (13) that lists the inventory of routers and switches in the network. Information on software version, equipment type, location etc. Also detailed information of router and switch ports with data on IP address / prefixes, vlans, port speed and duplex etc. CSV export supported. Includes a subnet matrix that gives a good overview of your allocated IPv4 and IPv6 prefixes. Also includes an overall downtime report for last month and a report that list unregistered network gear (based on CDP, soon LLDP, discovery).
- An IP Device Info tool (15) that serves as a dashboard presenting all collected information about a device. For switches and routers this includes a graphical layout of all ports showing link speed, duplex, vlan and status. A separate view displays the link history of switch ports thus giving an overview of the switch port utilization ratio.
- A device history tool (14) that displays all occurred events for a physical device (a given serial number).
- A threshold monitor (7) that gives alarms based on high load / high error rates or severe CPU load etc. The threshold monitor is highly configurable through the Threshold Manager web interface. The monitor understand states and will prevent alarm flapping by using hysteresis.
- A module monitor (5) that detects outage of switch or router components, i.e. individual switches in a switch stack or modules in a chassis.
- A service monitor (6) that reports on service outages. Support the most important services; ssh, http(s), imap(s), pop, smtp, smb, rpc, dns, smb, dc, rpc, dhcp, ftp, smb, mysql, postresql, oracle, radius. Can easily be expanded to support more services.
- A general event system (8) that processes all events, including alarms from external systems. Alarms from external systems are either sent as snmptrap to the NAV snmp trap daemon or as email to NAV's mailin system.
- A flexible alert system (9), where each NAV user can adjust his own profile (using the tool alert profiles, 21) with fine-grained control options. Currently support for sending email, SMS and jabber alerts. The profiles can be made to adjust the volume and types/severities of alarms wanted, this as a function of time and day of the week.
- A status page (22) that shows the current status of all events.
- A switch port configuration tool, portAdmin (10), that lets the NAV user change interface description and vlan values of switch ports. The tool uses SNMP write to perform its job.
In addition:
- A message system that displays operational messages to IT support staff and end users.
- A maintenance tool to put devices on maintenance for a planned time period and thus suppress alarms.
- A Cisco Syslog Analyzer that structures and lets you search syslog messeges from Cisco devices.
- A general mechanism for authentication and authorization of NAV users. Supports LDAP and Active Directory. Use the user adminstration tool to manage users and on a group level set the appropriate authorization level. NAV administrator can “sudo” to other users to see/adjust their setup.
NAV answers your questions
NAV is developed by network engineers with years of experience in operating large campus networks. NAV development has been going on for more than 12 years. Our priority has always been; implement the feature we lack most first. The overall objective has been indisputable:
- Reduce overall downtime, be even better, be ahead, work proactive.
To illustrate how NAV might help you in your work environment, here are some questions you might ask yourselves. NAV can answer them for you:
- What is the current status of our network and system operations? Is the network running properly? How are the servers (and their services) doing?
- What traffic volumes do we have? Are there any bottlenecks, if so, where? What are the traffic trends? Where should we upgrade first?
- What does the network look like? How is it interconnected? What is the scope of the various vlans / subnets? Where is server X connected?
- Do we see any traffic storms? In what direction does traffic flow?
- Which organizational units do we serve? Which IP prefixes do they occupy? How many machines do they have on a maximum/average? How are we utilizing our (precious) IP address scope (on the individual subnet level and on the global level)?
- How many computers are connected totally? How many of these are student PCs? How many are staff computers?
- What are the movements in the network of laptop Y that seems to be compromised. Where has he been the last 90 days? Where is it now?
- What type of network equipment do we have in our network? What kind of switches and routers, how many of each, where are they located? What software and hardware versions are they running? How many modules are there in the various stacked and chassis based switches? Are there any free, or almost free, modules? Help me get the overall picture, I need to expand switch Z and are looking for spare parts…
- Do we have any duplex problems? Do we have high error rates on any switch ports? Do we see packet drops?
- Just now we have a hardware failure or an unpredicted power outage… or a massive DDOS attack has just started… Please send me a SMS alarm on my mobile (but only send the most severe alarms after work hours). Which router has high CPU load? What devices are down? What seems to be the root cause here?
- I would like to inform end users and IT support staff at the faculties of this unfortunate event, or of another planned outage. I will use the NAV message system and put a message on the NAV home page.
NAV does not cover everything...
NAV helps you with many things, but not with everything (surprised?). You will always need a set of tools, no tool will cover every aspect of network management. And, of course, above all, you need knowledge of how to design and configure your network, how to troubleshoot etc.
Here are some areas where NAV does not help you:
- NAV is primarily a monitoring tool NAV and is not used for configuring your network equipment. There are however two important exceptions (NAV uses SNMP write in these two cases):
- The port blocking tool Arnold
- The PortAdmin component of IP Device Info that lets you configure vlan values and port descriptions of switch ports.
- NAV is not the Oracle in Delphi that will pinpoint all errors in your network. NAV tries to discover serious errors, but is by no means perfect. There are still things that need to be discovered by other means than NAV.
- NAV does not give you a precise report on how to solve a problem. NAV gives alerts / clear indications that something is wrong and must be corrected. You will often have to look closer at the problem, for instance by using CLI on a unit or using other tools.
- NAV does not give you end-to-end traffic data. NAV gives you traffic load for each interconnection in your network, but does not know the origin of the traffic nor where it is going. This means no end-to-end information with IP-addresses and TCP/UDP port numbers. Netflow or RMON2 may help you more with this. We recommend that you complement NAV with a netflow analysis tool; i.e. NfSen.